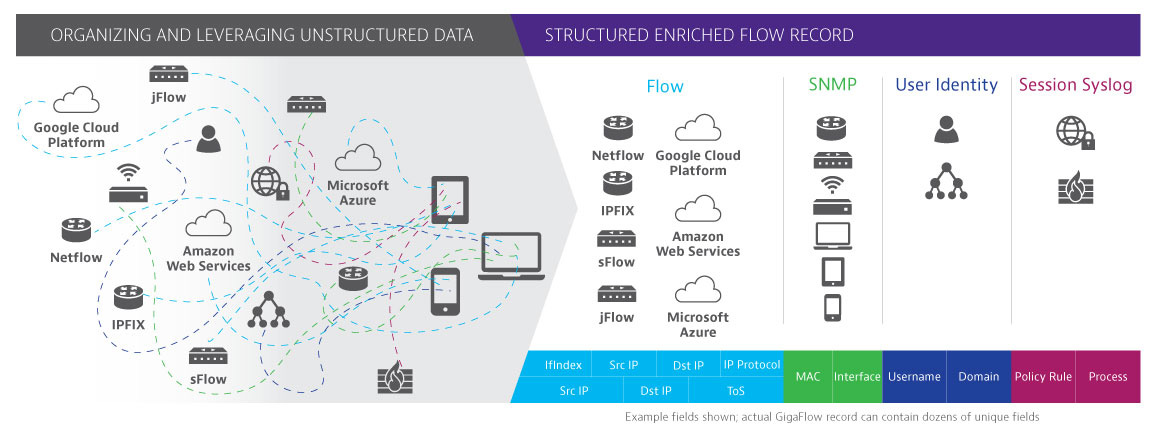
The growing number and variety of devices and applications across today’s hybrid IT environment are becoming increasingly difficult to manage — whether related to IoT, SD-WAN, cloud migrations or remote users at the network edge. Observer GigaFlow solves the pervasive end-user experience, performance, and security challenges in these dynamic environments by intelligently stitching traditional flow, SNMP, user identity, and session syslog data into an enriched flow record. It strengthens existing security measures by adding another layer of protection and peace-of-mind that your network infrastructure is well defended.
GigaFlow processes mountains of unstructured data and delivers enriched flow records that provide in-depth details on network device types, connectivity, traffic control, and usage patterns. This information is maintained at the individual user, over time across all communication traversing the environment from any point of view making it particularly valuable for NetOps and SecOps teams.
VIAVI brings the network to the table and exposes the infrastructure and traffic clearly to all business stakeholders serving as the go-to platform for every IT team.
Feature and Benefit Summary: